The cryptocurrency landscape was rattled by a significant security breach involving Ledger's Connect Kit, a widely used tool for connecting crypto wallets to decentralized applications (dApps). This incident, which unfolded rapidly, highlighted vulnerabilities in the crypto infrastructure and the importance of rigorous security protocols.
The Initial Breach
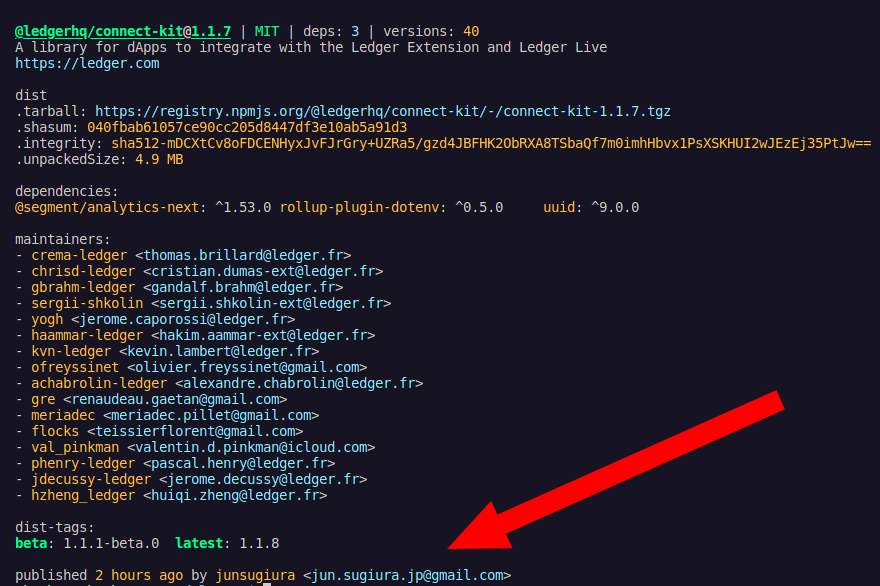
The saga began with the compromise of the Ledger Connect Kit due to a phishing attack targeting a former Ledger employee's NPMJS account. Malicious versions of the Ledger Connect Kit (versions 1.1.5, 1.1.6, and 1.1.7) were published, designed to redirect funds to a hacker’s wallet.
🚨We have identified and removed a malicious version of the Ledger Connect Kit. 🚨
— Ledger (@Ledger) December 14, 2023
A genuine version is being pushed to replace the malicious file now. Do not interact with any dApps for the moment. We will keep you informed as the situation evolves.
Your Ledger device and…
This vulnerability posed a significant threat, as it potentially allowed for the unauthorized draining of funds from users' wallets when interacting with affected dApps.
Ledger's Rapid Response
Upon discovering the breach, Ledger's technology and security teams responded swiftly, deploying a fix within 40 minutes. The malicious file was live for approximately 5 hours, but the window for potential fund drainage was believed to be under two hours.
FINAL TIMELINE AND UPDATE TO CUSTOMERS:
— Ledger (@Ledger) December 14, 2023
4:49pm CET:
Ledger Connect Kit genuine version 1.1.8 is being propagated now automatically. We recommend waiting 24 hours until using the Ledger Connect Kit again.
The investigation continues, here is the timeline of what we know about…
Ledger coordinated efforts with WalletConnect to disable the rogue project and began the process of propagating a genuine and verified version of the Connect Kit (version 1.1.8).
Addressing the Aftermath
In the aftermath of the breach, Ledger took several measures to ensure such an incident does not recur. The access of the connect-kit development team on NPM was restricted to read-only, preventing direct pushes of the NPM package. Ledger also rotated internal secrets for publishing on GitHub.
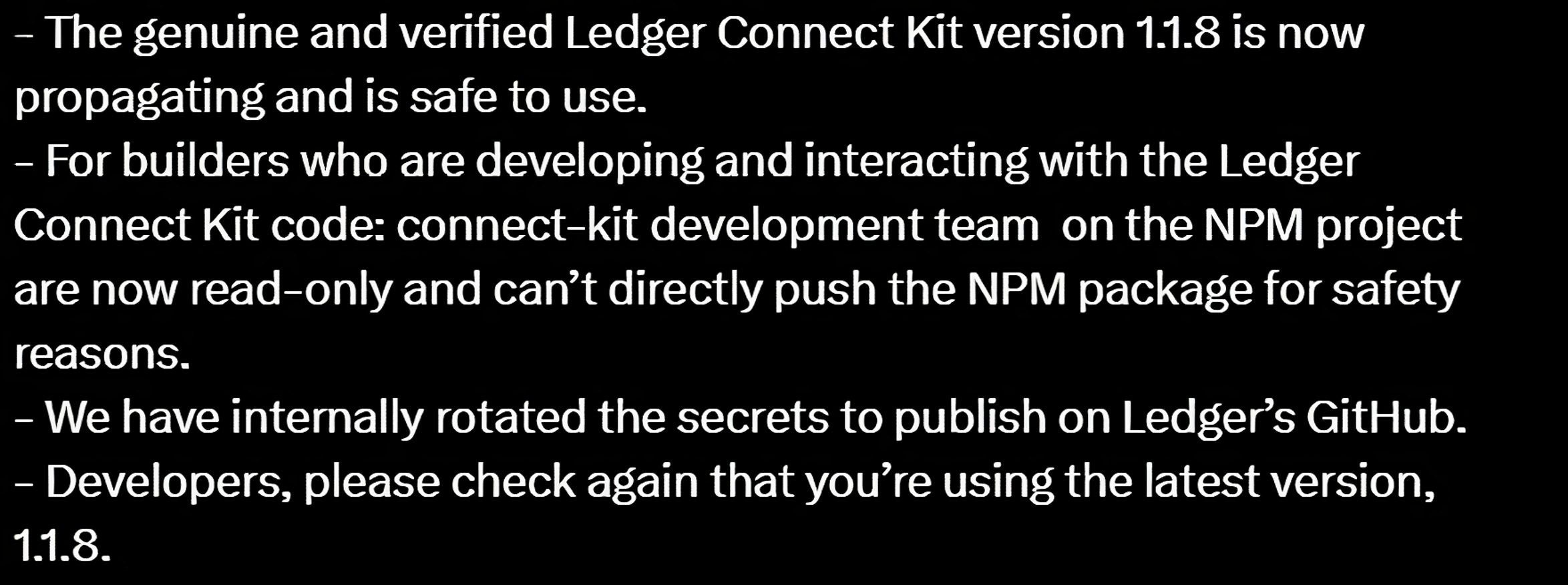
Developers were advised to update to the latest version (1.1.8) of the Connect Kit. Moreover, the bad actor’s wallet address was reported and made visible on Chainalysis, with Tether freezing the actor's USDT to mitigate further damage.
Community Concerns
The fact that a former Ledger employee's compromised account led to a major security breach has sparked widespread discussion and concern.
Please explain why a FORMER employee has an active key to publish stuff? pic.twitter.com/15SZe7Gu6G
— Legendary (@Legendary_NFT) December 14, 2023
Community members are questioning the adequacy of Ledger's internal security protocols, particularly regarding the management of access rights for former employees. In an industry where security is paramount, the maintenance of stringent access controls is a critical factor in preventing unauthorized intrusions and breaches.
Ledger's Commitment to Security
Throughout the crisis, Ledger emphasized the importance of security practices, particularly the Clear Sign protocol. Users were reminded to always verify transaction details on their Ledger devices.
Ledger’s proactive engagement with affected customers and collaboration with law enforcement agencies for the investigation underscored their commitment to user security and trust. The company’s response to this incident serves as a reminder of the ongoing challenges and the necessity for vigilance in the dynamic world of cryptocurrency.


